Your Chief Information Security Officer (CISO) has directed tighter security for obvious reasons. IBM’s pervasive encryption seems to be the direction many shops are moving to protect the integrity of the billions of dollars transacted on mainframes. But how do we get in front of the mainframe impacts or even know which methods might meet security requirements at lower cost?
Stated more to the point, what recourse does the performance and capacity team have when higher demand in the TCP/IP address space occurs as mainframe encryption is rolled out to the applications?
Mainframe Security – It’s Simple!
The CISO’s directive is a strategic and simple direction. However, most enterprise application portfolios encompass Windows, Linux, z/OS, and other operating systems; there are web servers, database servers, message brokers, and more. Data is transferred around in packets with file transfers, asynchronous messages, transactions, and more. Just enumerate those choices across the 50 to 200 applications and just do it now! Riiight?!
In this blog I’ll share an actual use case that reveals why it’s not so easy, as well as some encouragement to shine a light on your mainframe network traffic.
Step 1: Unlock the Critical Visibility into Encryption Status and Options
A more complete understanding of network traffic flows can help prepare for future migrations, which is critical to proactive planning. Seeing the details of all sorts of encryption options, the traffic sources, and detailed traffic metrics help expose where those impacts are being felt. Nobody wants a ‘surprise’ from the hardware and software costs of adding more processors when the hardware already has crypto co-processors. So, what’s going on?
IntelliMagic’s Todd Havekost has reviewed this extensively in a zAcademy webinar and articles in Cheryl Watson’s Tuning Letter. Beginning with z/OS 2.3, IBM provides the capability to have an entirely new level of visibility into the encryption status of all network traffic to and from your z/OS systems. This is enabled through z/OS Encryption Readiness Technology (zERT), which makes this data available in SMF 119 records.
Because managing network encryption is such a critical need, and the potential visibility provided by zERT summary data is so well-designed and comprehensive, Todd considers the introduction of zERT SMF 119.12 records to be “perhaps the greatest advance in SMF data since CPU Measurement Facility (CPUMF) began providing instrumentation of processor cache metrics through SMF 113 records in 2008.”
A solution like IntelliMagic Vision takes the SMF 119 data and automatically generates interactive charts that are rated against IBM Redbook best practices. Taking it a step further, drill downs are built into the solution to enable deep dive analysis, and report customizations are simply a matter of a few clicks. Figure 1 shows a rated IntelliMagic Vision before/after chart comparing Elliptic Curve Cryptography Activity by LPAR one week apart.
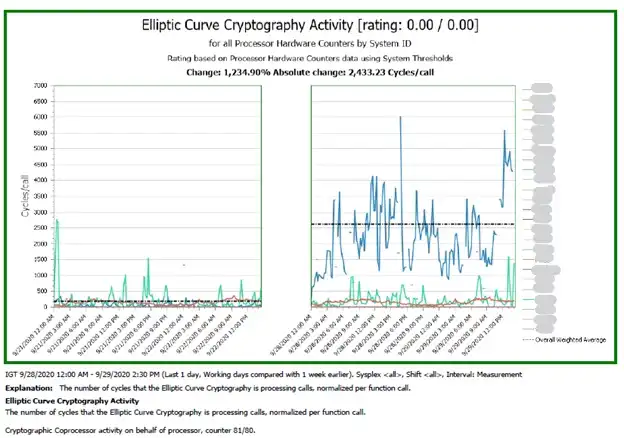
Figure 1: A rated report on Elliptic Curve Crypto Activity by LPAR comparing to prior week
Step 2: Identify and Isolate Encryption Activity
Once you have a solution like IntelliMagic Vision that allows you to unlock the critical encryption data embedded in the SMF records, the next step is to identify and isolate the new encryption activity occurring at your site.
Diving deeper into some of the standard IntelliMagic Vision zERT Reports shows a corresponding jump in short connections. This change may be related to the additional cipher activity handshaking in security sessions.
Note the description in Figure 2: “The count of connections that lasted less than 10 seconds. This information is from the SMF field SMF119SS_SAInitLifeShortConnCnt and SMF 119SS_SAEndLifeShortConnCnt. It is described in the IBM TCP/IP documentation as follows: the count of short connections for the life of this security session at the beginning of the summary interval. Short connections are connections that last less than 10 seconds. This value is only meaningful when SMF 11SS_SAIPProto indicates TCP, for other protocols this value is empty. IntelliMagic reports the average of the begin and end values for the interval.”
A performance specialist doesn’t have to know all the ins and outs of how security and network are working within zOS to see there is something going on.
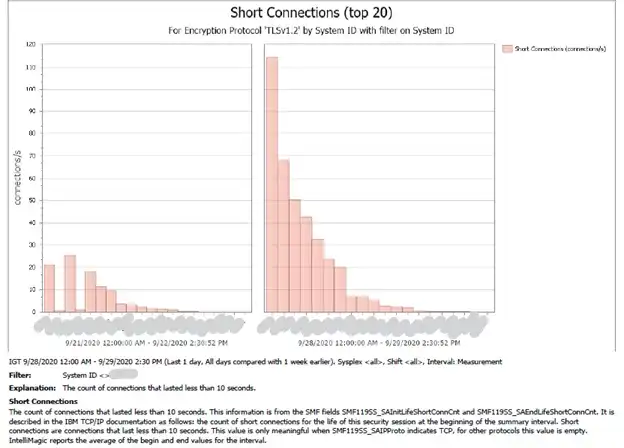
Figure 2: Short connections by LPAR comparing to prior week_LI
Further drilldowns of specific traffic to mainframe services (address space level, port level, IP level) can provide visibility of the traffic as it migrates from unencrypted to encrypted traffic. Particulars of each traffic flow, including the encryption protocols can help gauge the impacts as application security migrations proceed.
Use Case: New CPU Demand in TCP/IP Address Space
After rolling out mainframe encryption at their site, one of our customers encountered an unexpected spike in CPU demand in the TCP/IP address space.
Using IntelliMagic Vision’s standard reporting, the impacts from an application enabled security feature were identified, and this enabled actions to resolve the issue before costs escalated further. The effects of the change were easily demonstrated using the compare feature as seen in Figures 1 and 2.
The key observation correlated TCP/IP consumption with the calls to regenerate RSA digital signatures (by LPAR and CEC). These metrics were quickly exported from IntelliMagic Vision and combined to show an extremely high correlation in the TCP/IP CPU consumption with the higher RSA calls.
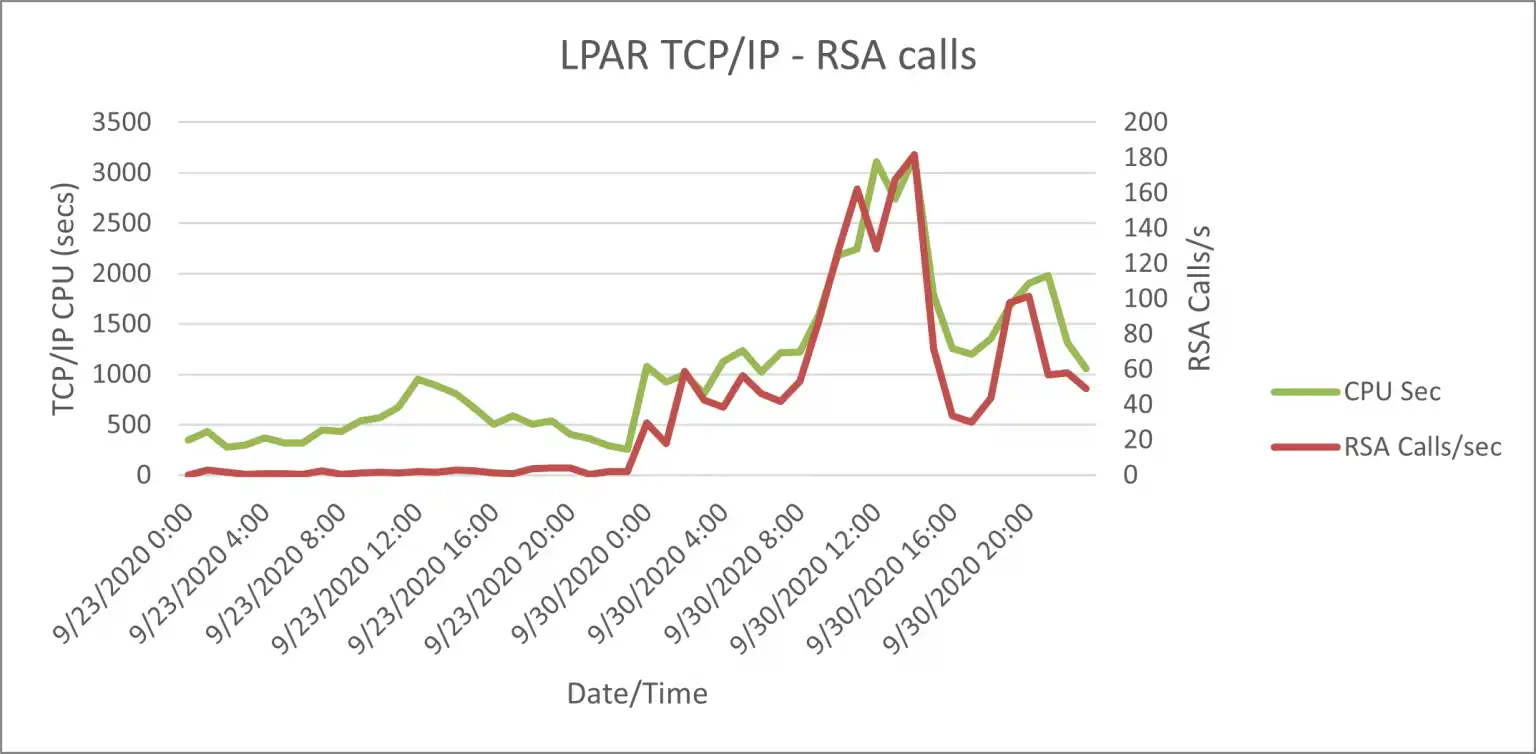
Figure 3: Hourly summarized TCPI/P type 30 data & TCP/IP calls from type 70 data exported
Further analysis showed that the z15 has a much lower cost for RSA generation calls than the z14. These details can help guide a more effective roll out of mandated security requirements and/or prevent unnecessary application security feature usage. Cost is always a consideration and helps guide security policies toward lower cost, while meeting security requirements will improve the value of your contribution to the enterprise.
Shine a Light on Your Encryption Activity
This use case demonstrates several keys to help meet your CISO’s strategy and protect your customers’ data. Shining a light on encryption activity will help avoid mistakes and keep your security improvement program on track.
We would welcome an opportunity to help you with a z/OS TCP/IP Encryption Compliance Analysis. Our services team using IntelliMagic Vision would also be happy to help you explore a fuller view of your enterprise from security to disk replication performance. Let’s shine a light together on the challenges you face so you can keep the lights on.
This article's author
Share this blog
Related Resources
Performance Analysis Leads to Improved Mainframe Security
Common views across technical silos helps foster effective communication and delivers timely responses to infrastructure and application changes without sacrificing safety.
What's New with IntelliMagic Vision for z/OS? 2024.1
January 29, 2024 | This month we've introduced updates to the Subsystem Topology Viewer, new Long-term MSU/MIPS Reporting, updates to ZPARM settings and Average Line Configurations, as well as updates to TCP/IP Communications reports.
Leveraging zERT and Other SMF Data to Manage and Optimize Network Encryption | IntelliMagic zAcademy
Given the importance of security in today’s world, managing network encryption is a critical requirement for almost every z/OS environment.
Book a Demo or Connect With an Expert
Discuss your technical or sales-related questions with our mainframe experts today


 Jack Opgenorth
Jack Opgenorth